CSRF protection
In version 8.3.5 of WebMail Lite, we have rewritten CSRF protection. This protection is enabled by default, but it may require additional configuration of your webserver. One of the indicators is the following message:
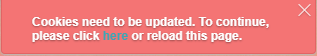
Typical reason is that web server is not configured for sending authentication headers through. To work around that, we're now shipping the product package with .htaccess file containing the following lines:
RewriteEngine on
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization},L]
NB: This file assumes that you're running Apache web server and mod_rewrite module is enabled for it. If you're getting Error 500 when accessing WebMail Lite installation, make sure mod_rewrite is enabled. Depending on your web server configuration, you may need to make changes to its main configuration file or virtual host definition.
(On a sidenote, the same .htaccess file includes configuration directives protecting data directory from external access - so if .htaccess file doesn't affect webserver configuration for some reason, it's strongly recommended to look into that.)
If you wish to be certain that CSRF protection is working on your installation, download a test file, unpack it into root folder of WebMail Lite installation and open it in a different tab of the same web browser you have WebMail Lite open and logged into. If all the lines in the report text are green, that means CSRF protection test is completed successfully.
If you're having troubles reconfiguring your environment to make CSRF protection work, you can disable it by setting CsrfTokenProtection to false in data/settings/modules/Core.config.json configuration file.
(Not Recommended! Do at your own risk!)
 MailBee.NET Objects .NET email components: SMTP, POP3, IMAP, EWS, Security, AntiSpam, Outlook, Address Validator, PDF
MailBee.NET Objects .NET email components: SMTP, POP3, IMAP, EWS, Security, AntiSpam, Outlook, Address Validator, PDF  MailBee.NET Queue Easy-to-use .NET service to deliver e-mails in the background
MailBee.NET Queue Easy-to-use .NET service to deliver e-mails in the background  MailBee Objects ActiveX email components: SMTP, POP3, IMAP, S/MIME
MailBee Objects ActiveX email components: SMTP, POP3, IMAP, S/MIME  MailBee Message Queue Queue-based background sending of emails
MailBee Message Queue Queue-based background sending of emails  WebMail Pro PHP Webmail front-end for your existing mail server, with personal calendar, contacts, and mobile sync
WebMail Pro PHP Webmail front-end for your existing mail server, with personal calendar, contacts, and mobile sync  WebMail Pro ASP.NET Webmail front-end for your existing mail server, with calendar sharing and global contacts
WebMail Pro ASP.NET Webmail front-end for your existing mail server, with calendar sharing and global contacts  ActiveServer Premium addon which brings ActiveSync support to WebMail Pro and Aurora
ActiveServer Premium addon which brings ActiveSync support to WebMail Pro and Aurora  Aurora Corporate Groupware system for businesses and providers
Aurora Corporate Groupware system for businesses and providers  Aurora Files Your personal cloud storage
Aurora Files Your personal cloud storage  Triton Transactional and newsletter emails sending solution
Triton Transactional and newsletter emails sending solution  MailSuite Pro for Linux Mail server (MTA) bundled with WebMail Pro for a complete solution
MailSuite Pro for Linux Mail server (MTA) bundled with WebMail Pro for a complete solution  Unified Messaging Solution Technology platform which provides telecom users with a feature-rich messaging portal
Unified Messaging Solution Technology platform which provides telecom users with a feature-rich messaging portal