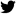The product now supports integration with Cloudflare Turnstile on login screen, ensuring that only humans can log into Aurora Corporate interface. Compared to
integration with Google reCAPTCHA, it provides more smooth integration, with little to no distraction for real users.
The module is available at https://github.com/afterlogic/aurora-module-webclient-cloudflare-turnstile-plugin and you can install it by following the instructions for adding a module.
Once you have the module installed, navigate to adminpanel and press "Update configuration" button in Database Settings screen to ensure the configuration file is created.
The functionality is configured by editing CloudflareTurnstileWebclientPlugin.config.json configuration file found in data/settings/modules directory, by default it looks like this:
{
"Disabled": [
false,
"bool",
null,
"Setting to true disables the module"
],
"SiteKey": [
"",
"string",
null,
"Site key obtained at Cloudflare Turnstile website"
],
"SecretKey": [
"",
"string",
null,
"Secret key obtained at Cloudflare Turnstile website"
],
"WhitelistIPs": [
[],
"array",
null,
"List of IP addresses CAPTCHA is never be displayed for"
],
"IncludeInMobile": [
true,
"bool",
null,
"If true, the module is used in mobile version of the interface"
],
"IncludeInDesktop": [
true,
"bool",
null,
"If true, the module is used in desktop version of the interface"
],
"SystemLogPath": [
"",
"string",
null,
"Location of the system log file, if empty then Aurora logs are used"
]
}
You'll need to supply SiteKey and SecretKey values, those are obtained at Cloudflare Turnstile web site. The key pair can be obtained for specific domain or set of domains. Please note that we support all the Turnstile modes currently available (managed, non-interactive and invisible).
WhitelistIPs configuration option can hold a list of IP addresses verification will never be requested for. Addresses need to be supplied as array, like this:
"WhitelistIPs": [
["192.168.0.6", "192.168.0.9"],
CIDR notation like "192.168.2.0/24" is supported as well.
If value for SystemLogPath is supplied, all failed login attempts will be recorded in the specified log file. The file needs to exist, and webserver/PHP needs to have permission to write into that file.
 MailBee.NET Objects .NET email components: SMTP, POP3, IMAP, EWS, Security, AntiSpam, Outlook, Address Validator, PDF
MailBee.NET Objects .NET email components: SMTP, POP3, IMAP, EWS, Security, AntiSpam, Outlook, Address Validator, PDF  MailBee.NET Queue Easy-to-use .NET service to deliver e-mails in the background
MailBee.NET Queue Easy-to-use .NET service to deliver e-mails in the background  MailBee Objects ActiveX email components: SMTP, POP3, IMAP, S/MIME
MailBee Objects ActiveX email components: SMTP, POP3, IMAP, S/MIME  MailBee Message Queue Queue-based background sending of emails
MailBee Message Queue Queue-based background sending of emails  WebMail Pro PHP Webmail front-end for your existing mail server, with personal calendar, contacts, and mobile sync
WebMail Pro PHP Webmail front-end for your existing mail server, with personal calendar, contacts, and mobile sync  WebMail Pro ASP.NET Webmail front-end for your existing mail server, with calendar sharing and global contacts
WebMail Pro ASP.NET Webmail front-end for your existing mail server, with calendar sharing and global contacts  ActiveServer Premium addon which brings ActiveSync support to WebMail Pro and Aurora
ActiveServer Premium addon which brings ActiveSync support to WebMail Pro and Aurora  Aurora Corporate Groupware system for businesses and providers
Aurora Corporate Groupware system for businesses and providers  Aurora Files Your personal cloud storage
Aurora Files Your personal cloud storage  Triton Transactional and newsletter emails sending solution
Triton Transactional and newsletter emails sending solution  MailSuite Pro for Linux Mail server (MTA) bundled with WebMail Pro for a complete solution
MailSuite Pro for Linux Mail server (MTA) bundled with WebMail Pro for a complete solution  Unified Messaging Solution Technology platform which provides telecom users with a feature-rich messaging portal
Unified Messaging Solution Technology platform which provides telecom users with a feature-rich messaging portal